TL;DR
- A governance failure in Unleash Protocol allowed an attacker to steal $3.9 million with out compromising the underlying blockchain or elevating rapid alarms.
- The attacker exploited the multisig system to execute an unauthorized contract improve, bypassing controls and transferring funds instantly.
- After the assault, the funds have been fragmented and despatched to Twister Money. Unleash paused operations and is reviewing its governance processes and key administration practices.
A governance failure in Unleash Protocol enabled an attacker to steal $3.9 million in person funds. The incident didn’t compromise the underlying blockchain or Story Protocol validators however highlighted how vulnerabilities in contract administration can result in important losses.
How the Assault Labored
The assault originated in Unleash’s multisig system. The attacker obtained administrative permissions usually requiring approval from licensed signers and used them to execute an unauthorized contract improve. This transformation altered how withdrawals have been processed, bypassing any governance controls and permitting the attacker to maneuver funds instantly out of the protocol.
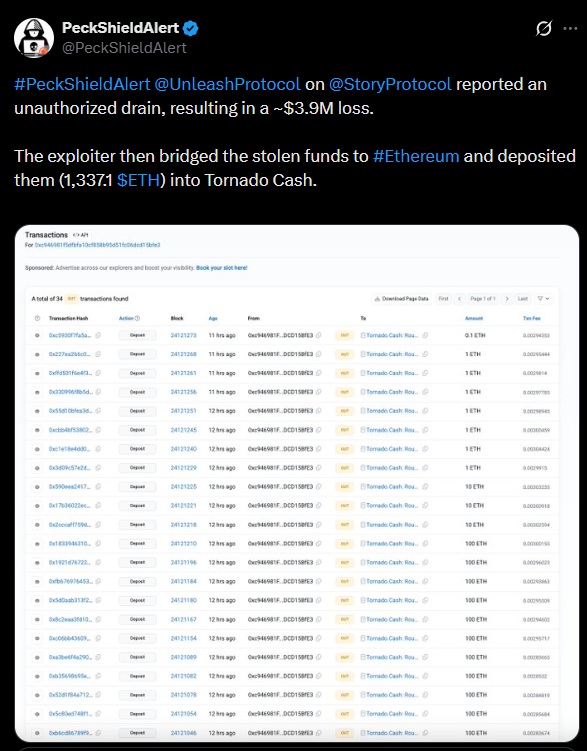
Affected belongings included WIP, USDC, WETH, stIP, and vIP. All withdrawals occurred via the altered contract relatively than regular person interactions. After extraction, the funds have been transferred to Ethereum and break up throughout a number of transactions. A complete of 1,337.1 ETH was deposited into Twister Money, a deliberate try to obscure the path and hinder on-chain monitoring.
Unleash responded instantly by pausing all operations to stop additional losses. The group is now working with forensic and safety consultants to grasp how governance protections have been bypassed. They’re reviewing multisig signer exercise, key administration, and inner contract administration processes. Customers have been suggested to not work together with the contracts till additional official directions are issued.
Governance methods can change into factors of weak point. Even when the bottom blockchains are safe, permission administration and contract upgrades in decentralized functions stay susceptible. Inside controls, contract replace procedures, and signer oversight are as crucial because the safety of the underlying community.
Unleash Continues Investigating
Unleash additionally emphasised that the investigation stays ongoing and that any closing conclusions will likely be communicated via official channels. This episode underscores that decentralization doesn’t inherently assure security. Weak governance, unsupervised upgrades, and concentrated permissions can price tens of millions.
Safety relies upon not solely on the bottom code however on the management and administration of each layer of the appliance. With out energetic oversight, any decentralized protocol can change into a straightforward goal