A cryptocurrency dealer has misplaced practically $50 million in USDT after falling sufferer to an tackle poisoning rip-off, a method that exploits transaction historical past relatively than good contract flaws. Blockchain safety corporations stated the incident highlights how routine pockets habits can expose customers to large-scale losses.
In an X put up, on-chain analytics agency Lookonchain reported that the sufferer transferred 49,999,950 USDT to an attacker-controlled pockets on Dec. 20. The funds had simply been withdrawn from Binance and have been meant for the dealer’s personal tackle. As a substitute, they have been redirected to a visually comparable tackle created by the attacker.
Deal with Poisoning Rip-off Exploits Spoofed Addresses
The incident started with a check transaction. The dealer despatched a 50 USDT check transaction to verify the vacation spot tackle. Shortly after, an automatic script generated a spoofed pockets designed to resemble the authentic tackle.This step marked the beginning of the tackle poisoning rip-off.
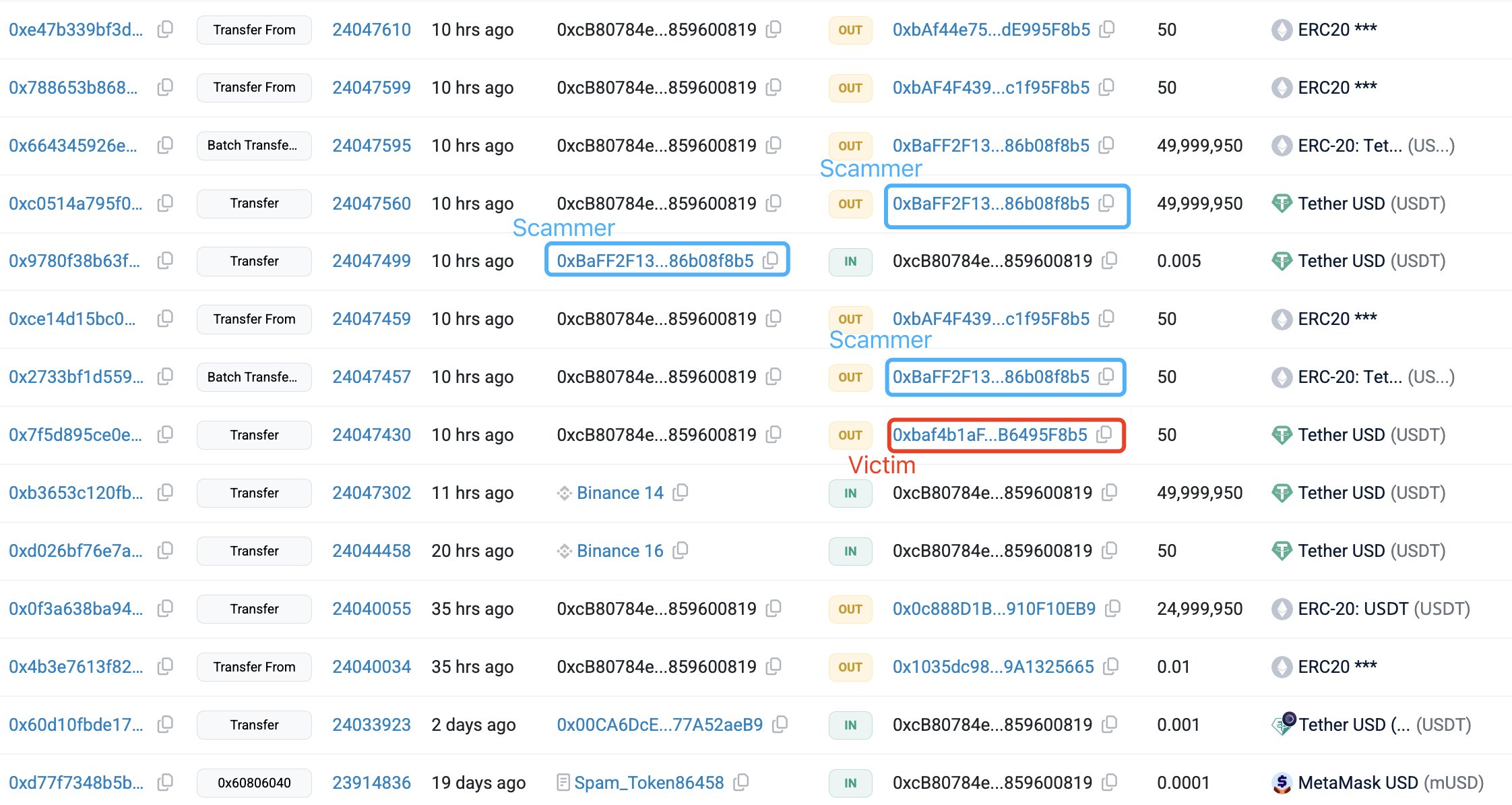
The fraudulent tackle shared the identical opening and shutting characters because the meant pockets, with variations confined to the middle of the string. Many pockets interfaces shorten these center characters, lowering visibility throughout routine checks.
By exploiting this show habits, the attacker despatched small transactions from the lookalike tackle to the sufferer’s pockets. This inserted the faux tackle into the transaction historical past, inflicting it to seem authentic throughout later transfers.
When the dealer later copied an tackle from their historical past to finish the total switch, the lookalike tackle was doubtless chosen by mistake. Etherscan knowledge exhibits the check fee was despatched at 3:06 UTC. The inaccurate $50 million transaction adopted roughly 26 minutes later, at 3:32 UTC.
Stolen Funds Moved By DAI, ETH, and Twister Money
Blockchain safety firm SlowMist reported that the attacker moved shortly with the intention to reduce restoration danger. In half-hour, the $50 USDT was exchanged for DAI by by way of MetaMask Swap. The choice was strategic as a result of Tether can freeze USDT if it’s related to illicit exercise, however DAI doesn’t include any centralized freezes.
The DAI was then transformed by the attacker to roughly 16,690 ETH. Roughly 16,680 ETH was deposited into Twister Money. The mixer was an try and obfuscate the transaction trails, the standard step subsequent to an tackle poisoning rip-off.
Upon executing the transaction, the sufferer despatched an on-chain message to the attacker by a $1 million white-hat bounty. The supply demanded the compensation of 98% of the stolen cash. There was no public acknowledgement or reply. The safety corporations stay lively monitoring the tackle poisoning rip-off.
In response to Chainalysis, the incident contributes to a yr of rising crypto thefts. Losses in crypo hacks 2025 exceeded $3.4 billion, extra than the earlier yr. A type of, a February breach of Bybit by North Korea-linked actors, totaled about $1.4 billion and was the biggest crypto theft ever.






